It seems like hardly a week goes by these days when we don’t hear about yet another data breach or newly-discovered exploit in widely used software. Bad neighborhoods have existed on the Internet for a long time, but danger now seems to present itself at every turn. There’s malware lurking all over the place, email accounts are constantly being hijacked to send spam, and websites are being broken into to steal information or cause damage to a firm’s reputation.
Sadly, many of these incidents are happening because people aren’t taking basic steps to stay safe. Technologies like HTTPS and SNI exist to encrypt data and user sessions, but they aren’t as widely used as they ought to be.
NPI has always been a security and privacy conscious organization, and we have repeatedly spoken out here in support of good cybersecurity hygiene.
But we know that speaking out isn’t enough. Real leadership means setting a good example for others to follow. We have to walk our talk.
And today, we’re doing just that.
With so many grim developments on the cybersecurity front lately, it’s our pleasure to be the bearers of some good news for a change.
Over the past year, we’ve invested in some important improvements to our web infrastructure, with the last pieces going into place this week. Thanks to these improvements, which are made possible due to the generosity of our loyal supporters, we are now able to encrypt — by default! — all visits to our core network (nwprogressive.org), which includes the Cascadia Advocate and In Brief.
What does this mean? It means that when you type in nwprogressive.org or navigate here from a link or bookmark, your browser will communicate with our server over an encrypted connection.
How can we guarantee this? Because we’re no longer giving anybody the option of connecting to nwprogressive.org insecurely.
Try typing the address for this blog right now, and our server will redirect you. It’ll require you to connect over a secure port, and you’ll see the prefix change to HTTPS if you didn’t put in. The idea here is to make sure that data sent by our web server to your computer gets scrambled as it travels across the Internet using Transport Layer Security (TLS). Likewise, if you fill out a form on our site and send us data, the contents will be encrypted while in transit to our server.
We have actually been using HTTPS to manage NPI’s websites for quite a long time, but now HTTPS is the default on the frontend as well as the backend.
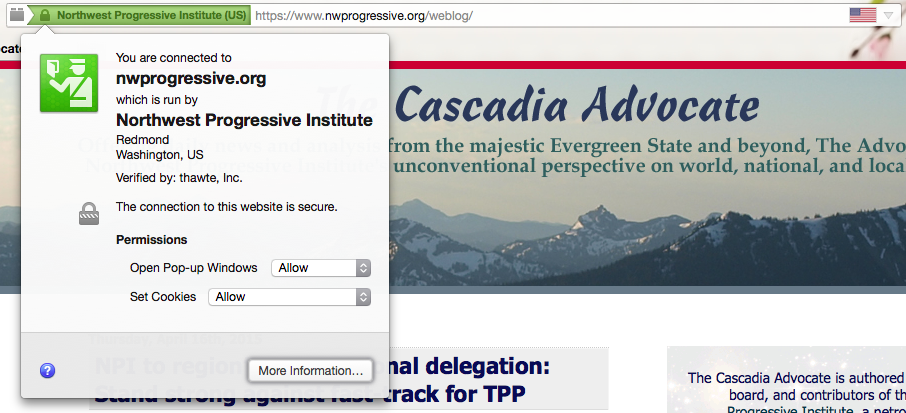
You can tell that the connection is secure because a padlock icon will appear in your address bar. Additionally, because we have invested in an extended validation certificate, the padlock icon should be green, and part or all of your address bar may also appear green. If you’re using a desktop browser, you’ll see NPI’s name.
For example, in Mozilla Firefox on a Mac:

Depending on what browser and operating system you have, the address bar will look different. The green background might stretch across the entire width of the bar, or it might only appear behind the text that says Northwest Progressive Institute. Regardless, some part of the bar will turn a shade of a green, as you can see from the following compilation of browser address bars:
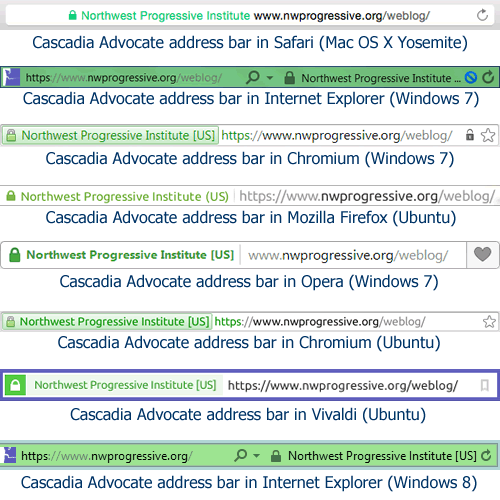 Not many organizations go to the trouble of investing in extended validation certificates. They can be pretty expensive (though we secured ours at a very good price) and a bit of a bother to set up.
Not many organizations go to the trouble of investing in extended validation certificates. They can be pretty expensive (though we secured ours at a very good price) and a bit of a bother to set up.
But EV certificates have one critically important advantage over regular secure certificates: they’re immune to spoofing in two of the most-widely used browsers in the world. Those are Firefox and Chromium (which Google Chrome is based on).
Coincidentally, Chromium/Chrome and Firefox also happen to be the browsers of choice for the vast majority of people visiting NPI’s network of websites. That much we know from consulting our server logs and site statistics.
So, most of you reading this benefit from our investment in an EV certificate.
Certificate spoofing can certainly be malicious (with an intent to cause harm) but sometimes it is done by institutions we trust — like our employers or our schools — that want to spy on us. Researcher Steve Gibson explains:
Any corporation, educational institution, or other Internet connectivity provider who wishes to monitor every Internet action of its employees, students or users—every private user ID & password of every social networking or banking site they visit, their medical records, all “secure” email… EVERYTHING — simply arranges to add one additional “Pseudo Certificate Authority” to their users’ browsers or computers.
It’s that simple.
By “pseudo certificate authority”, Steve means a fake entity invented by the corporation or institution that wishes to spy on its users, as opposed to a real certificate authority like Symantec’s Thawte, Comodo Group, Trustwave, GeoTrust, or the newly-formed, free software community-backed Let’s Encrypt.
Consider Steve’s hypothetical:
For example, suppose that “Bendover Industries” installs a commercially available “SSL Proxy” (also known as an HTTPS or TLS Proxy). Then, as part of prepping computers for use inside their network, Bendover’s IT department simply adds one additional “trusted” Certificate Authority to each computer. That’s all it takes.
Now, whenever anyone inside Bendover’s network makes a “secure” connection to any remote public web site—their bank, Google Mail, Facebook, anything—that connection is intercepted by Bendover’s SSL Proxy appliance before it leaves the building.
On-the-fly, the SSL Proxy Appliance creates a fraudulent “spoofed” web server certificate in order to impersonate the intended remote web site, and it signs that fraudulent certificate itself using the signature of the also-fraudulent Certificate Authority that was previously planted inside the user’s browser or computer.
If this sounds villainous, well, that’s because it is. Do note that the technique Steve is describing can only be practically and readily implemented on computers that an institution controls. A personally-owned computer that an institution’s IT department doesn’t have access to can’t be tricked out with a pseudo-CA.
The consequences of this spoofing are pretty serious:
Instead of connecting to the remote web server, the browser is “securely” connected only to the local Proxy Appliance which is decrypting, inspecting, and logging all of the material sent from the browser. It inspects all content to determine whether it abides by whatever arbitrary policies the local network is enforcing. Its users have NO privacy and NO security. Or perhaps it just silently logs & records everything for possible future need. Either way, it has obtained full access to everything the user enters into their web browser.
While SSL/TLS interception cannot be prevented when a user doesn’t have control over the computer he or she is using, it can almost always be detected, because certificate spoofing results in a fingerprinting mismatch between the public key and the private key (which the institution running the pseudo-CA doesn’t know).
In the course of his research into certificate spoofing, Steve discovered, as I mentioned earlier, that EV certificates cannot be spoofed in Firefox or Chromium/Chrome, owing to the way that those browsers are made:
Since both Mozilla’s Firefox and Google’s Chrome/Chromium browser projects are fully open source, we were able to inspect the way EV certificates are validated.
They maintain their own private internal lists of trusted EV certificate authorities and will ONLY display the green EV coloration when the server’s certificate has been signed by a chain of certificates terminating in one of those known root authorities. This means that they cannot fall prey to EV spoofing the way Internet Explorer was designed to.
The EV handling within Opera and Safari are unknown. They are closed source browsers, and they do not appear to publish any formal statements about their handling of EV certificates. (If anyone does have any definitive information about Opera or Safari, please drop us a line.)
If the above is Greek to you, don’t fret.
Here’s the takeaway that you need to know: If you’re connecting to NPI’s website in an open source browser like Firefox or Chromium and your browser address bar doesn’t partially turn green, it means the connection is not fully secure.
The absence of the green field might occasionally be due to the presence of mixed content. That’s when a page you’re accessing over HTTPS loads embedded content like images or scripts over a regular ‘ol HTTP connection that isn’t secure.
We haven’t scoured every single page and post on nwprogressive.org yet to remove all of the hardcoded HTTP prefixes that may exist. But we’ve corrected enough that you should see the green field most of the time.
If you never see it, it’s quite possible that your secure browsing is being intercepted. To know for sure, you’d want to compare certificate fingerprints (if you know how… if you don’t, you could ask a tech-savvy friend, or contact us for assistance.)
When an institution lacks the power to sniff or intercept Internet traffic, it sometimes blocks use of HTTPS altogether, which is really unfortunate.
The Bellevue School District does this, for example. I know they do it because I’ve logged onto their guest Wi-Fi network before and discovered that it’s not possible to securely connect to any website. It doesn’t matter what it is.
Because this domain now only accepts traffic over HTTPS, it’s not going to load at all on a public Wi-Fi network where HTTPS is blocked. That’s a consequence we are willing to live with. None of us should be using an Internet service provider or Wi-Fi network where HTTPS has been blocked anyway.
Projects not hosted at nwprogressive.org are not yet set to require visitors to use HTTPS, but will be soon. Permanent Defense will be next — it already has its CA-issued certificate. After that, we’ll move on to Pacific NW Portal.
Making websites secure is hard work, so it may be a few months before we’re done. But the effort has been and will be well worth it.
If you have any questions or comments about the security upgrades we’ve made here, please don’t hesitate to get in touch or leave a comment here. In either case, your message to us will be transmitted over an encrypted connection!

Wow, I had no idea about certificate spoofing. Kudos to NPI for caring so much about the security and privacy of your visitors! Not enough webmasters do.
You’ve certainly set a good example for others. Thank you for doing this.